Managed XDR
Break down the silos with eXtended Detection & Response (XDR).
To stay ahead of sophisticated threats, we built our Managed XDR Service to enable a coordinated detection and response capabilities across all the security layers, including the network, cloud, and end-points. Our service is a combination of cutting-edge AI XDR solution and our global SOC processes.

Simplify your security stack. Streamline orchestration, automation, and response across the extended layers for broad visibility.
Visibility across the security spectrum
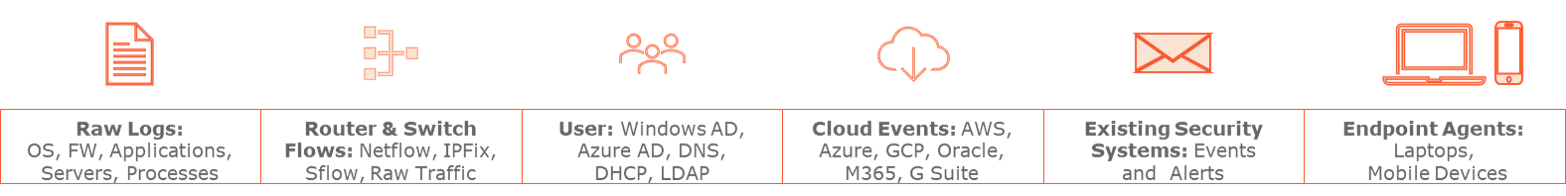
- Ingests raw streaming data to provide unparalleled real-time view of all assets applications, users and their interactions including logs, packets, flows, identities, and more
- Logically auto discovers and creates asset groups
- Detect IT misconfigurations
- Network Flow Analysis
AI and ML based analytics
- Proactively detects threats in real-time including event correlation, filtering and alerting
- Ransomware, Malware, Spyware, APTs
- Malicious Insider, compromised credentials, UEBA, privilege misuse
- Cloud Security: IaaS - AWS/Azure/GCP, PaaS, CASB, SaaS – O365/Azure
- Denial of Service: Bruteforce, Volumetric, Application Layer, Protocols
- Strict Policy Enforcement
- Vulnerability exploits: Data/IP Exfiltration, Apps, Firmware, Email, Web
- Intrusion Detection and Prevention Systems
- Threat detection across multi-cloud, on-premise, and hybrid environments
SOC analysts assisted by AI triage response
- Clear actionable steps to contain and eliminate threats in real-time
- Formalized and automated incident response workflows

We partner with you
- We actively perform Threat Hunting and leverage MITRE ATT&CK framework to classify and study attack methods
- Perform rapid forensic analysis and support
- We will not just alert and flee, but will stay with you through resolution

Continuous Compliance & Reporting
- HIPAA, PCI-DSS, NIST, GDPR, custom
- Executive and Operational Reports

Our service defends against a comprehensive set of attacks.
File Integrity Monitoring
EDR
Brute Force
Malware
Data Loss Prevention
Web Application/Email
Adversaries pry into web applications to access database, steal credentials, download malware or redirect user to malicious sites. Cybersecurity attacks and breaches are instrumented through web applications: Cross-Site Scripting, SQL Injection, Directory Traversal, Remote File Execution, Cross-Site Request Forgery and many more.
Ransomware
Detect at host where the ransomware payload tries to infect the endpoint host.
Insider Threats
Data Breach
Analysis of security related data from multiple angles – file usage, user activity and network traffic (applications, servers). Additionally, threat intelligence and vulnerability scan results play important roles in enriching context.
